Phillip Roberts and Giacomo Marchese | 17 September 2024
Have you ever stumbled upon a rental deal so good that you had to pinch yourself to believe?
Well, you’re not alone. Fortian security analysts recently discovered a fraud campaign leveraging fake rental properties affecting housing providers, their clients, and renters broadly. This campaign is a significant step up in complexity compared to historically observed fake property rentals, as this campaign incorporates brand impersonation via spoofed websites to deceive victims. Fortian observed threat actors creating fraudulent listings on Facebook Marketplace and potentially other property websites, offering seemingly legitimate rental properties in Australia.
The threat actors will employ social engineering to direct users to a malicious, attacker-controlled website that mirrors the appearance of a legitimate booking.com website. Once the victim reserves the accommodation, they will automatically receive an email with a fake invoice allegedly from booking.com requesting the victim to transfer the payment directly to the attacker-controlled bank account.
By creating a fake booking.com website that near-perfectly replicates the original, victims are more easily deceived into believing they are interacting with a trusted platform. This additional step of redirecting victims to the fake booking.com website aims to enhance the perceived credibility of the scam by exploiting the trust that people inherently place in well-known platforms.
This blog post will provide details of the campaign, the technical and social engineering techniques utilised, and recommendations for how to protect your organisation and clients from falling victim.
Targeting Vulnerable Populations The common theme seen across most threat campaigns is the ability to take advantage of victims who may be vulnerable to certain methods of extortion. In this campaign, the threat actor specifically targeted individuals seeking community housing, leveraging their urgent need for affordable accommodation.
Unlike typical malicious sites, which might be easily identified by poor design or obvious errors, the spoofed booking.com website in this campaign was a sophisticated replica of the legitimate booking.com website. It used HTTPS to appear secure and mimicked the real booking.com site closely. This high level of detail, combined with the use of a legitimate-looking domain name legitimises the appearance of the website.
This campaign differs from previously observed campaigns by exploiting the trust in well-established brands. By creating a near-perfect replica of booking.com, the threat actors capitalised on the victim's trust in the platform, making the scam more believable. The use of real property images and detailed fake invoices further enhanced the illusion of legitimacy.
From a technical standpoint, the attackers demonstrated advanced knowledge in several areas. They registered a domain name that closely resembled the legitimate Booking.com site, employed HTTPS to create the appearance of security, and used tiny URLs to obscure the true destination of the malicious links. Additionally, they utilized email hyperlinking techniques, where words or sentences in the email contained links that appeared legitimate but redirected users to the fake site. These methods show a higher level of sophistication and a deeper understanding of how to bypass common user safeguards.
Fake rental properties, sometimes referred to as phantom rentals, is not a new scam. However, in most historic cases a scammer will list a fake rental on a legitimate website and request a direct deposit from the victim before signing a contract. Generally, the scam will never leave the original legitimate property listing website. In the latest campaign observed by Fortian, scammers developed spoofed websites that masquerade as booking.com and allege that all payment and processes will be handled by booking.com. This campaign, while including the traditionally observed social engineering techniques, includes an additional step of redirecting victims to the fake booking.com website to enhance the perceived credibility of the scam.
On June 17, 2024, Fortian identified that a support worker of a client who operates in the Community Housing sector had interacted with a malicious URL which initiated multiple redirects before directing to a fake booking.com website. Fortian's investigation revealed that the URL had originated from an email chain forwarded to the support worker by a legitimate client of the housing provider.
This fraud campaign begins when the victim interacts with a Facebook Marketplace listing advertising a fake rental property. In this instance, the listing was for a property in Brighton, Melbourne, with a real address (redacted for the real owner’s privacy) and real pictures that were obtained by the threat from a legitimate years-old listing on realestate.com.au.
Reverse searching the images revealed that they were originally uploaded to a legitimate property listing on realestate.com.au from several years prior. The threat actor appeared to have taken the images, address, and parts of the description from the original listing. It is notable that the fraudulent Marketplace listing did not include any direct links to malicious websites. This helps bolster the perceived legitimacy of the listing.

The victim messaged the owner expressing interest in the property, and after a brief discussion via Facebook Messenger, the owner directed the conversation to email.
The email conversation is where the threat actor directs the victim to the malicious website. In this instance, the owner of the Marketplace listing used a generic Gmail email address (`andrew.luke342@gmail.com`) and employed social engineering to build rapport with the victim. They behaved cordially and professionally, initially requesting information from the victim about their age, occupation, family size, and if they own any pets.

After the victim provided this information the threat actor informed the victim that the booking would be handled by booking.com, then requested more detailed information including full name, date of birth, photo ID, and information regarding the desired rental period. While the information requested included sensitive personal information (PI), Fortian assess that the primary intention was to increase the perceived credibility of the scam.
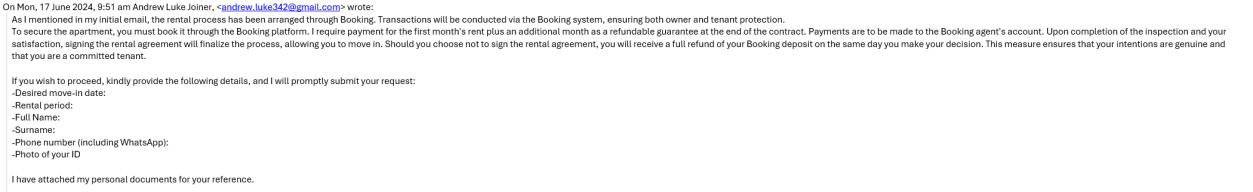
After the victim provided the requested information, the threat actor explained the terms and conditions of the rent and explained that the payments would all be handled by booking.com. This was another social engineering technique which leveraged the trust and authority of booking.com to provide assurance to the victim that this was genuine. The threat actor then sent the victim an email that included a hyperlink to the attacker-controlled website. The text read `booking.com/rooms/56734556/listings/`, but the hyperlink redirected to `https://tinyurl[.]com/2y7ess82`.
This was yet another spoofing tactic, making it appear as though the user was clicking a genuine booking.com URL contained within the email message. The Tinyurl redirect was also attempt to obfuscate the final URL redirect.

Clicking the Tinyurl link redirected to the URL ` hxxps[:]//booking.eu-apt-booking[.]homes/property-aid-63785823-label-gen-832513841233/691886813`, which is the final stage URL of the redirect that hosted the fake property rental.
This website had a domain similar [www.booking.com](http://www.booking.com/) that was registered only a few days prior to the attack, and replicated all the assets of the original booking.com website.
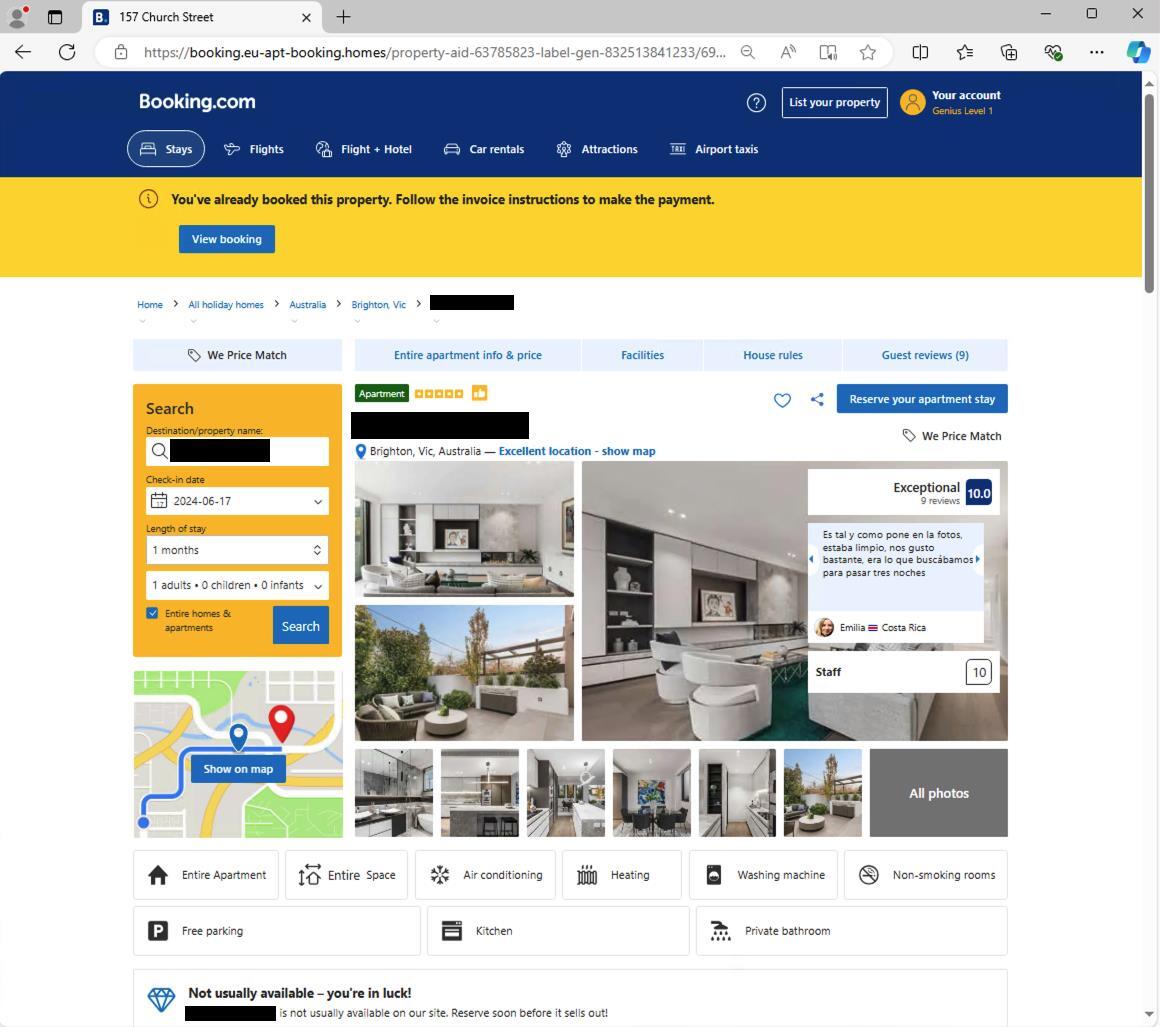
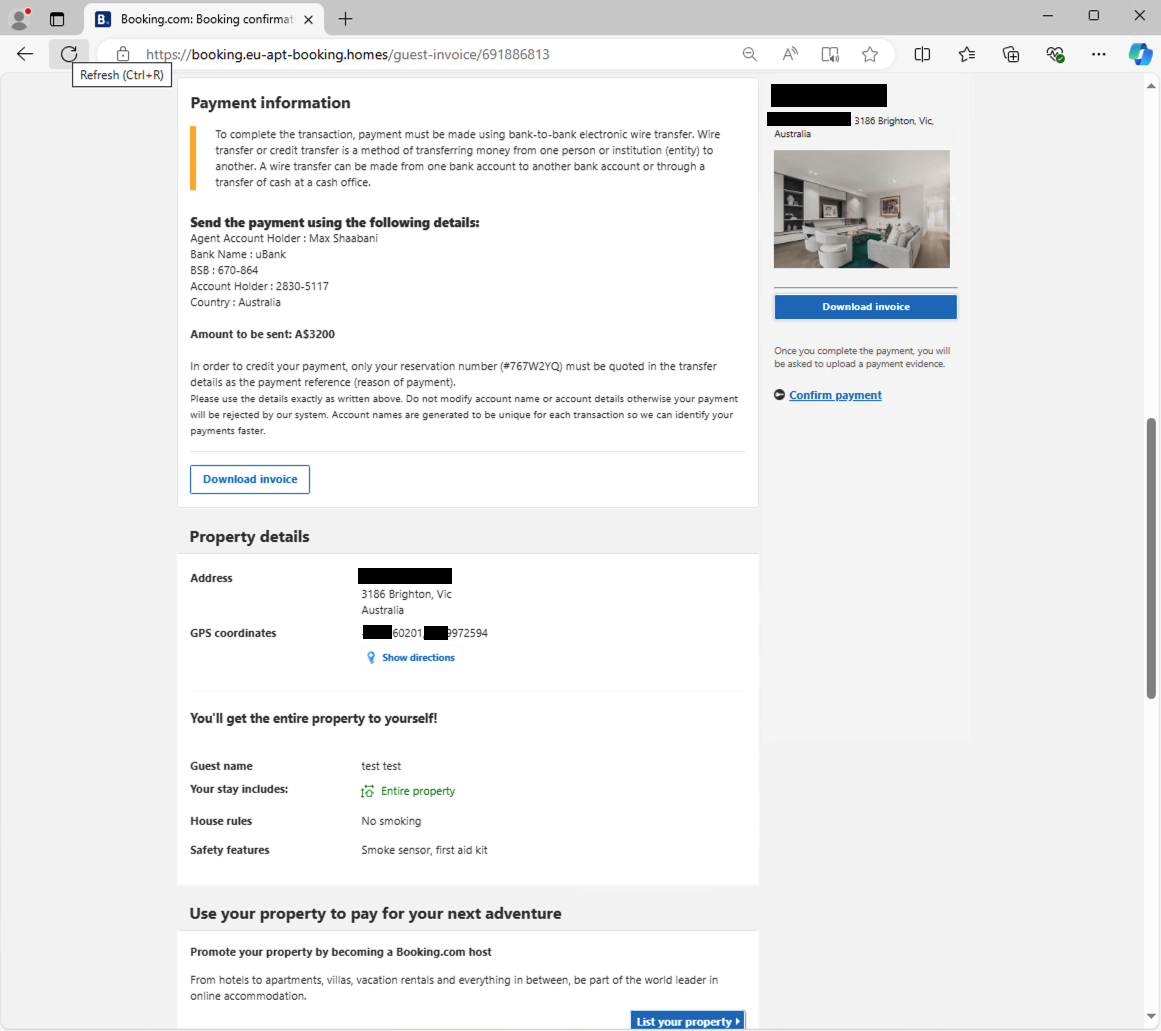
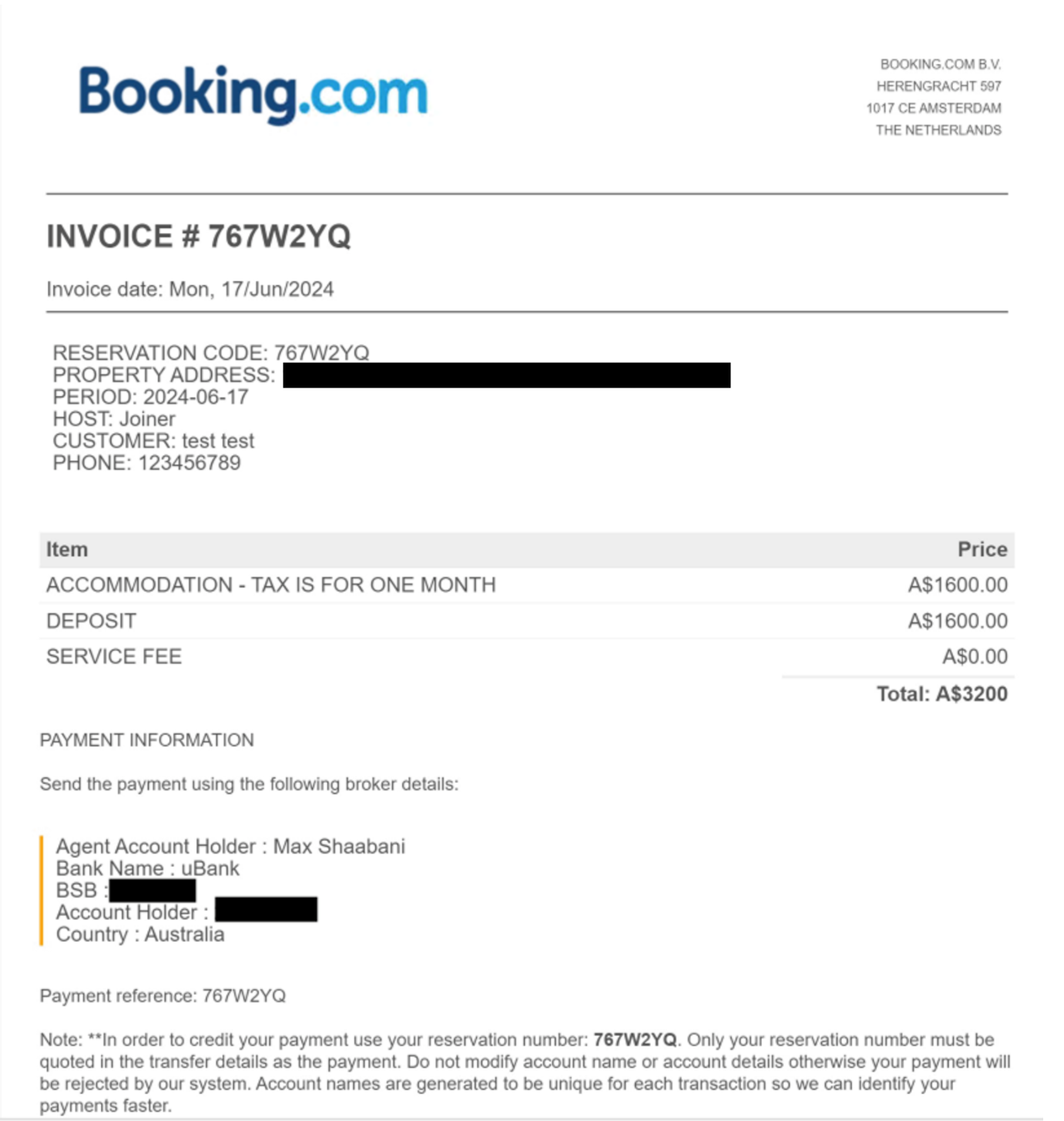
By following the prompts on the fake websites, the victim can reserve the accommodation. After doing so, they are redirected to a page on the attacker-controlled website with payment details and will receive an automatic email from the sender `booking[@]invitations-booking[.]com` with a fake invoice, purportedly from booking.com. In both cases, the payment details allegedly belong to booking.com, but in reality are associated with an attacker-controlled bank account. To maintain the illusion of legitimacy, the fake invoice dynamically included all details associated with the booking, including specified dates and the name and contact details submitted when “booking” the property.
Organisations can protect themselves from this campaign via a combination of technical security controls and user awareness training.- Organisations should provide security training to internal staff on how to spot spoofed websites and verify the authenticity of websites.
Attributes to look out for include:
From a technical control perspective, Fortian recommends:
This fake rental properties campaign highlights the evolving tactics of cybercriminals, who are becoming increasingly adept at creating convincing fraudulent schemes. The use of spoofed websites, social engineering, and the exploitation of trusted platforms like Facebook Marketplace and Booking.com illustrate the need for heightened vigilance and education among potential victims. Users should always verify the authenticity of property listings, scrutinize URLs, and be wary of unrealistic offers. By understanding the latest tactics employed by threat actors, individuals and organisations can better protect themselves from falling victim.
Indicator
Type
Description
andrew.luke342[@]gmail[.]com
Email address
Email address used in the initial email discussion between the threat actor and the victim. This email address provided the malicious link directing the victim to the attacker-controlled website
booking[@]invitations-booking[.]com
Email address
Email address that sent the automatically-generated invoice after booking the apartment.
https://tinyurl[.]com/2y7ess82
URL
Stage one malicious link
https://booking.eu-apt-booking[.]homes/property-aid-63785823-label-gen-832513841233/691886813
URL
Final stage malicious website hosting the fake property listing.
Request a consultation with one of our security specialists today or sign up to receive our monthly newsletter via email.
Get in touch Sign up!