Adrian Bole, Senior Consultant / Strategic Partnerships Manager (adrian@fortian.com.au) | May 11, 2020
Worried about ever-increasing attacks on your website? Looking for an easy way to cut out some of that attack traffic noise? Over the next two blog posts we’re going to use Imperva’s Cloud Web Application Firewall (WAF), (formerly known as Incapsula) to protect one of my web sites and then protect access to the Imperva console with Multi Factor Authentication (MFA) using Okta. The site we’ll be using as my guinea pig is https://itsecuritychina.com, a site I setup a few years back to occasionally re-post Chinese-related IT security news (you’ll note there isn't too much recent content – I’ve been lazy). It’s running on a self-hosted WordPress setup and, as we all know, WordPress is a fairly well targeted platform being regularly probed for vulnerabilities, therefore a great candidate to hid behind a WAF.
Now a WAF is not a silver bullet to protecting your website from bad guys – it’s a control to layer on once other basic security hygiene controls are in place:
Of course, there are many, many other security practices you can implement but that's just a few of the basics (I’m expecting feedback from you all on everything else I should have listed here – don’t be shy).
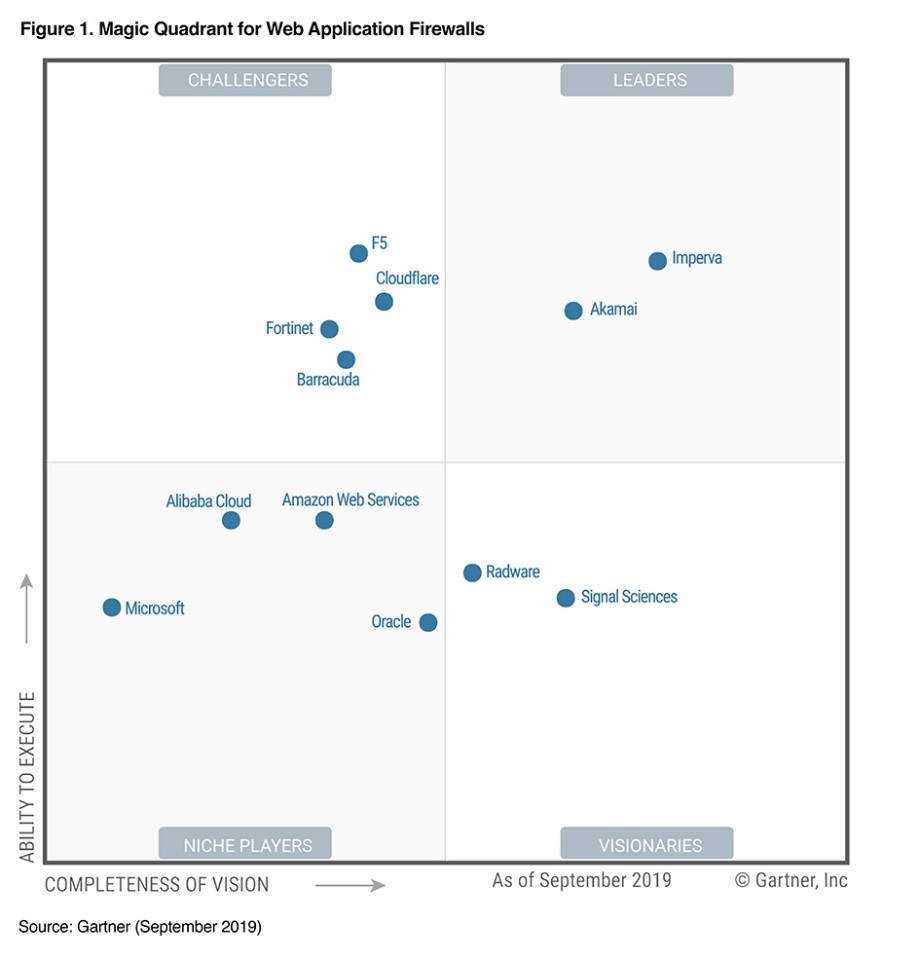
So why Imperva Adrian? There are many excellent WAF-as-a-service offerings you could use (AWS WAF, Google Cloud Armor, Akamai Kona, Azure Web Application Firewall, Securi, etc.) but today we’ll be using Imperva as, basically, that’s what I had an account for! Imperva they had scored very well in the technical evaluation during a market selection activity at a former employer, and if you like Gartner, it looks like they’re still not too bad (though they did have a few security issues of their own last year).
If you want to play along at home, you’ll need:
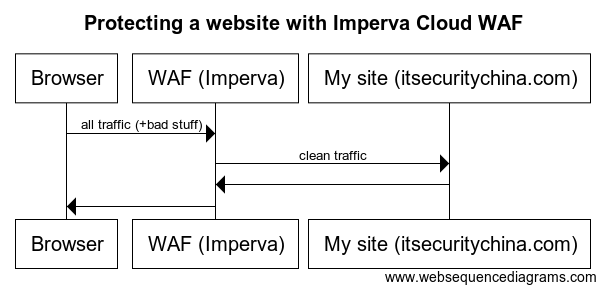
Here’s a simple sequence diagram for what our end state should look like
Let’s get onto the practical side.
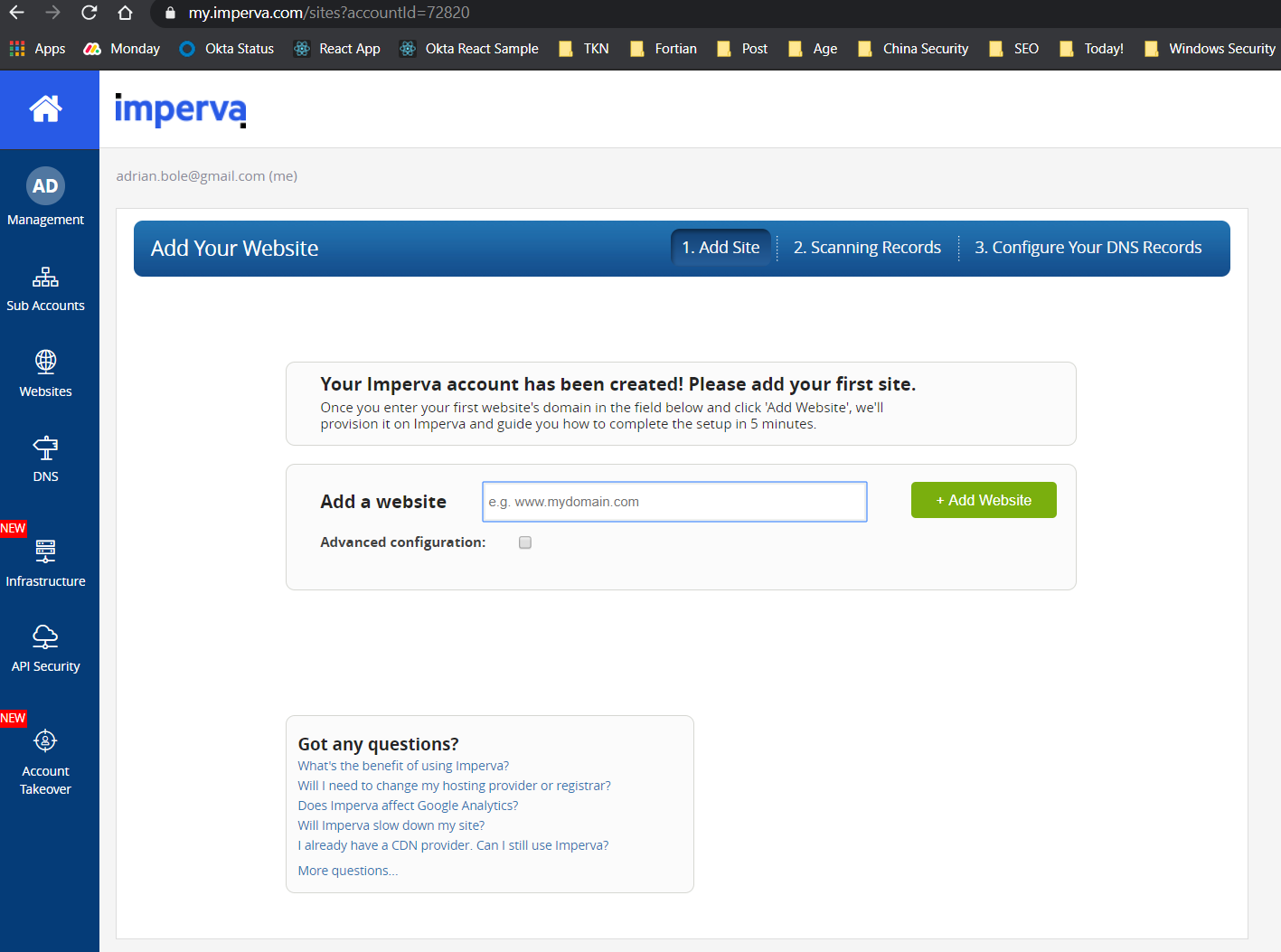
Step 1: Log into your Imperva account (my.imperva.com) and add your site
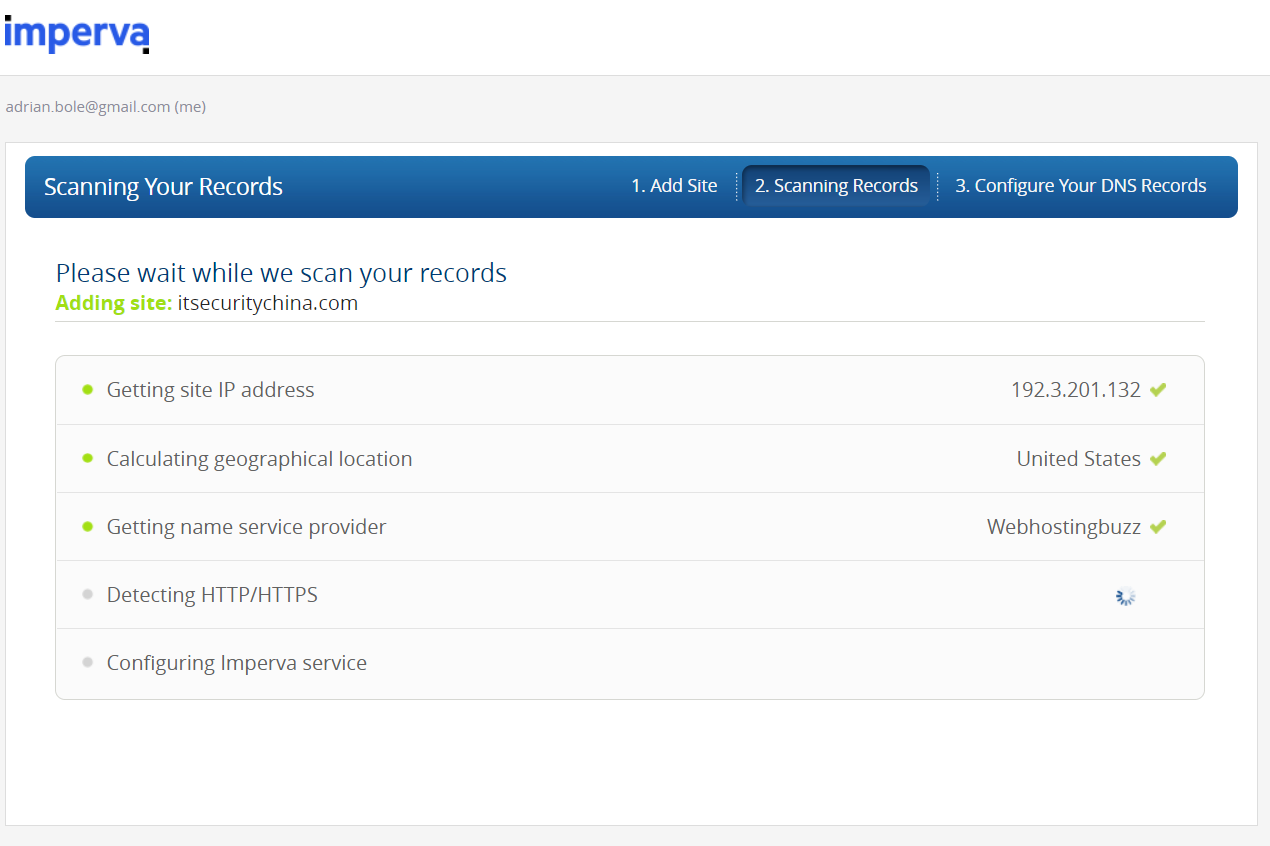
You should then see something like this. Click continue once it's found all your details.
In the next step we choose our approach for TLS. I'm going to choose to use in Imperva's TLS certificate because I’m lazy and don’t have a reliable mechanism to manage my own keys. To get an Imperva certificate, click start and then we need to step to prove we own our domain name.
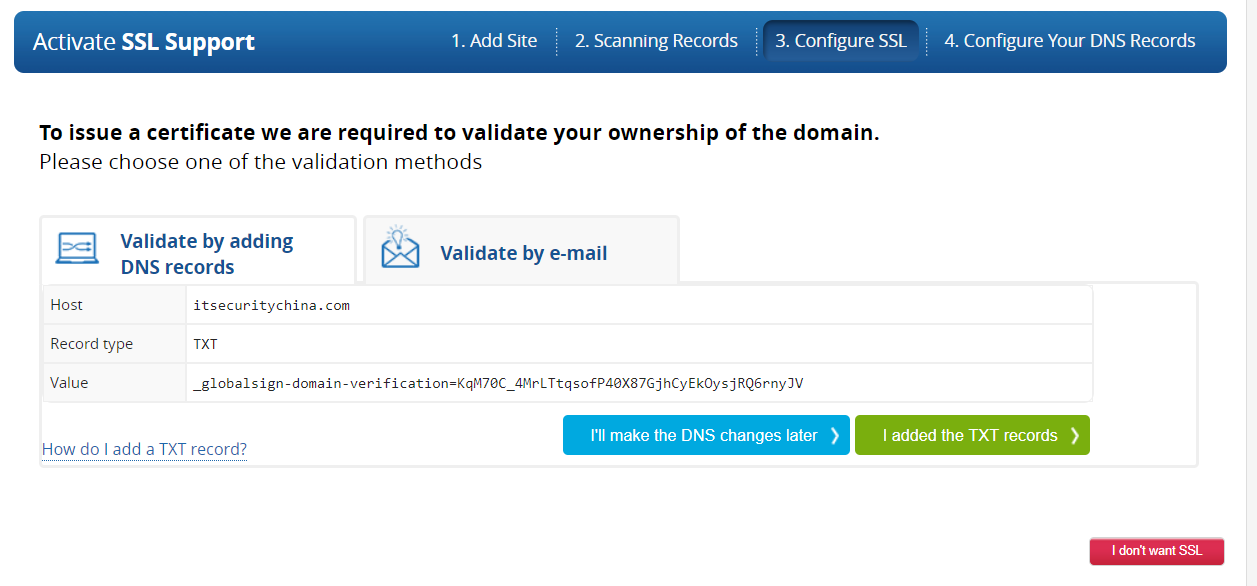
We are about to jump over to cPanel (or your other console of choice to manage DNS). Copy your TXT record line before you do.
_globalsign-domain-verification=blahblahblah…
Now log into cPanel over on your hosting provider, or wherever your DNS zone editor is going to be. Here's what my embarrassingly old version of cPanel looks like.
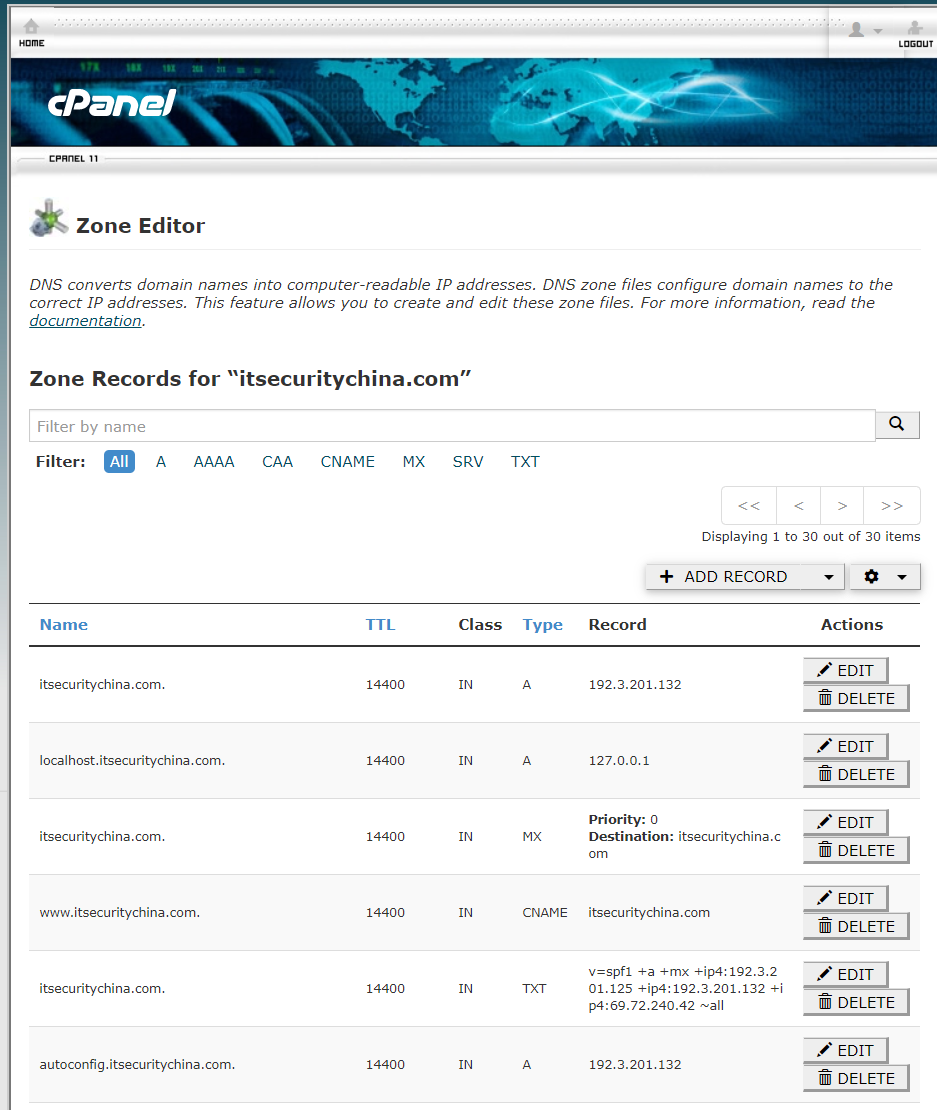
I clicked Add Record, entered itsecuritychina.com. (with trailing period) as the hostname and pasted in the TXT record contents from Imperva.
Let's jump back over to the Imperva site and see if it can see the record. Click on the "I added the text records" button and it will start a validation step.
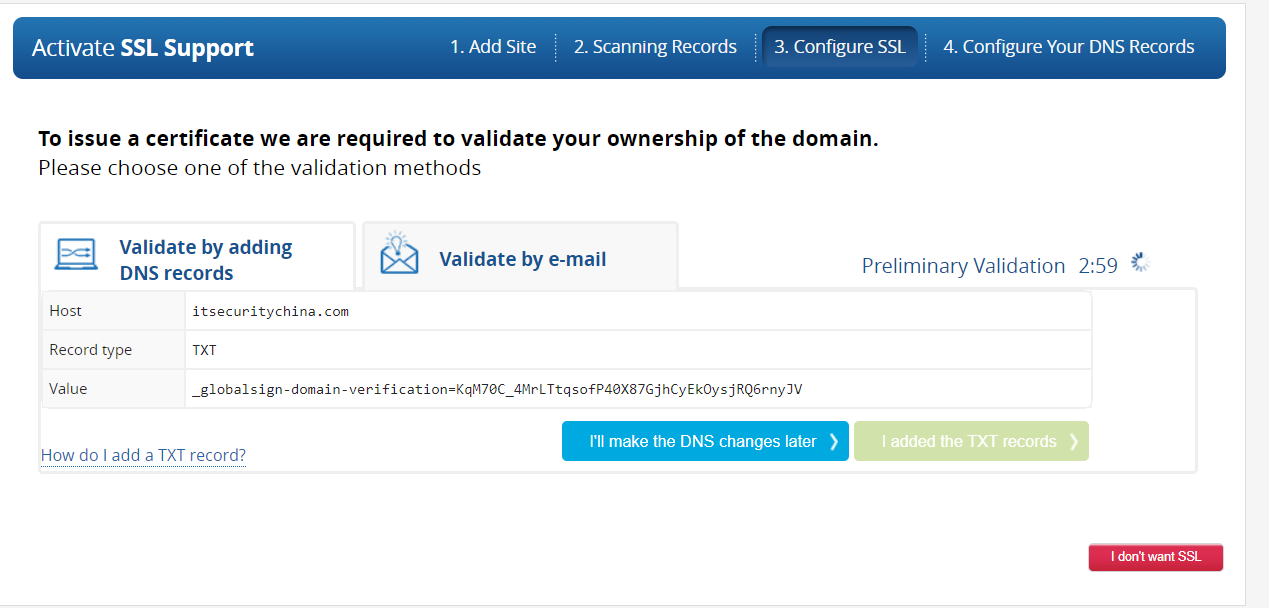
Now, as always, DNS can take a while to propagate and it may take some time before you see a success message here - be patient.
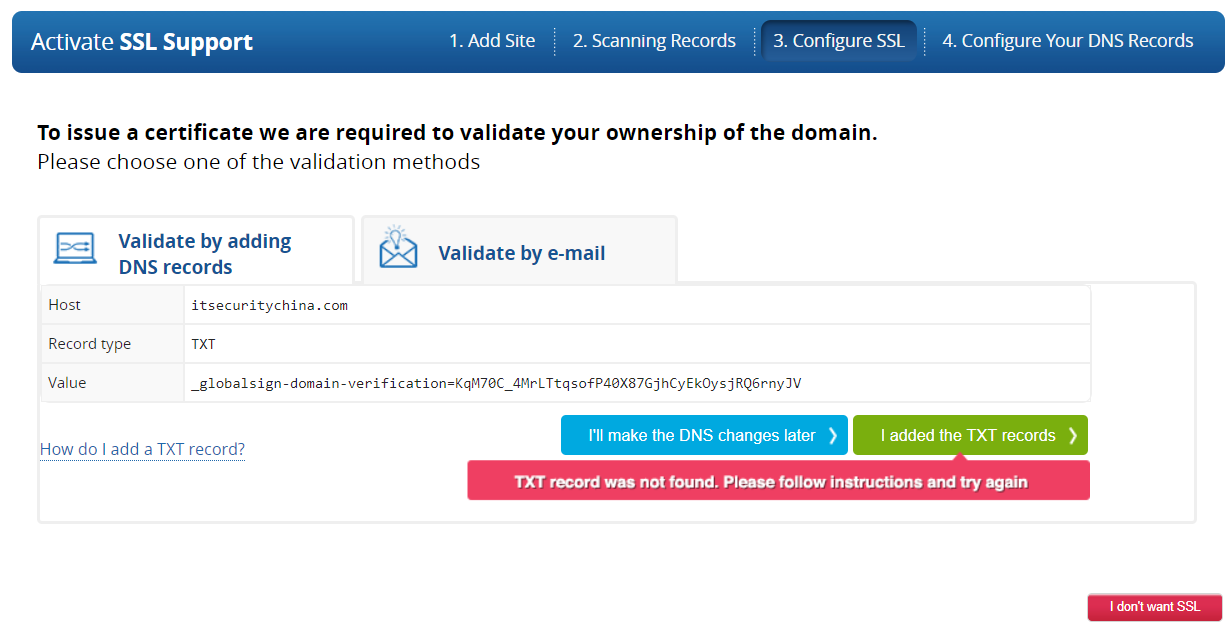
But soon our patience is rewarded - woo hoo! We have a “Certificate Approved” message. It’s still thinking so I assume it’s also creating the certificate.
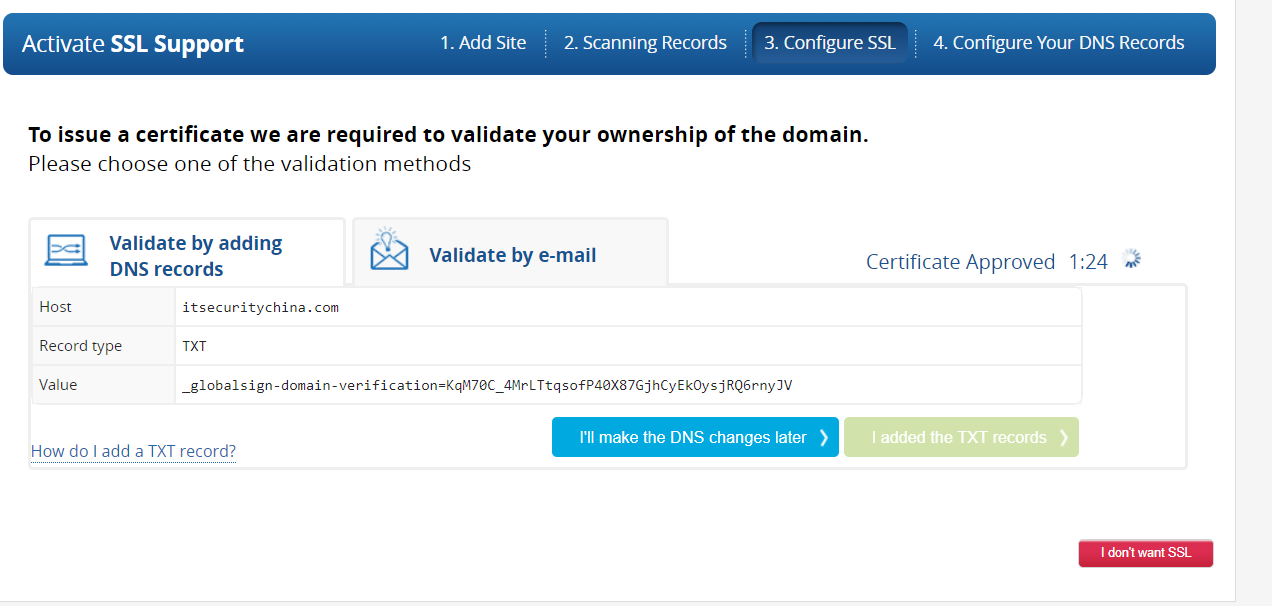
Looks like it will take a while longer.
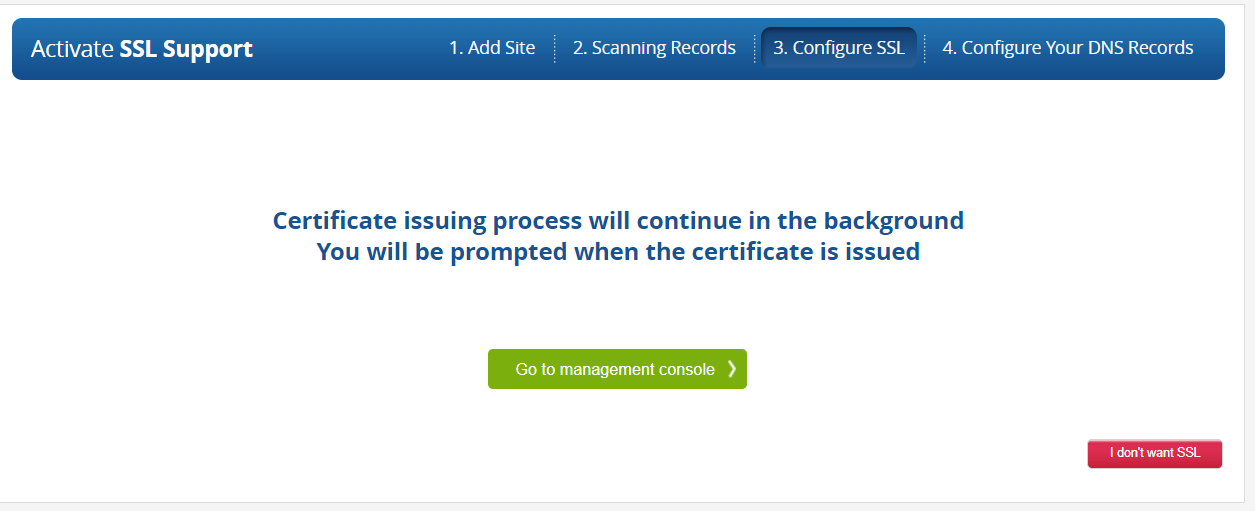
Go back to the management console and we should see our website now listed.
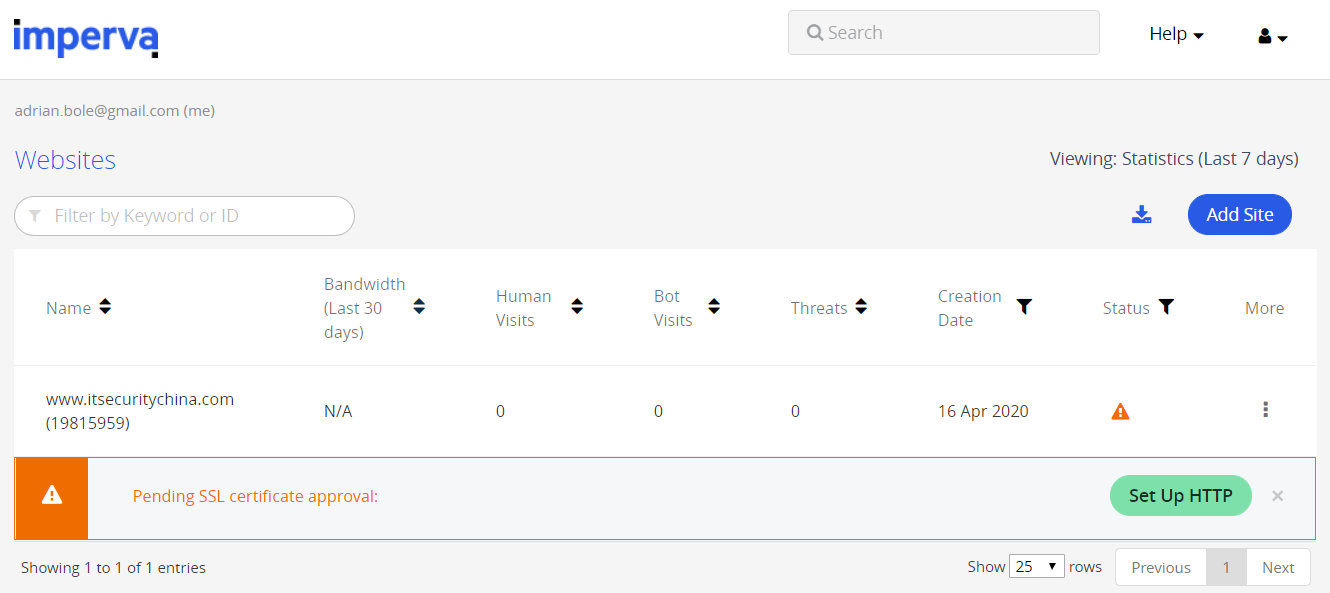
Let's hit it our site and see what happens.
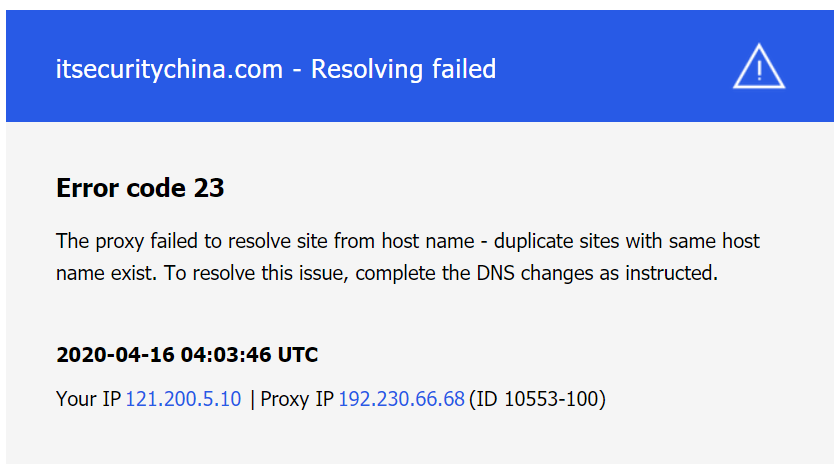
Well that doesn't look very good. We’re getting this message because while Imperva knows where our website is, our website doesn't really know it’s going behind Imperva. I’m impatient, so in the Imperva console, click the setup HTTP button. And drat! Looks Imperva is trying to keep us secure so reminds us a certificate is being generated and to wait patiently. So, it looks like at this point were actually stuck, let's go have a little break and we'll be back shortly.
Okay so about an hour has passed now and I've just received an email from Imperva that certificate generation has been completed with some handy DNS address to use in my cPanel DNS changes.
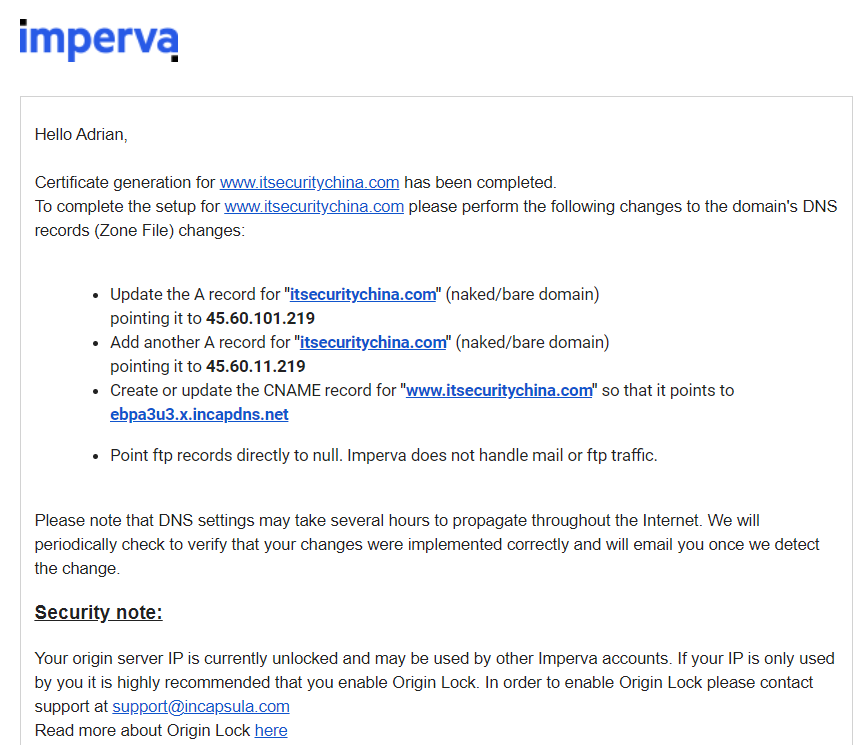
Over in the Imperva console this is what I see.
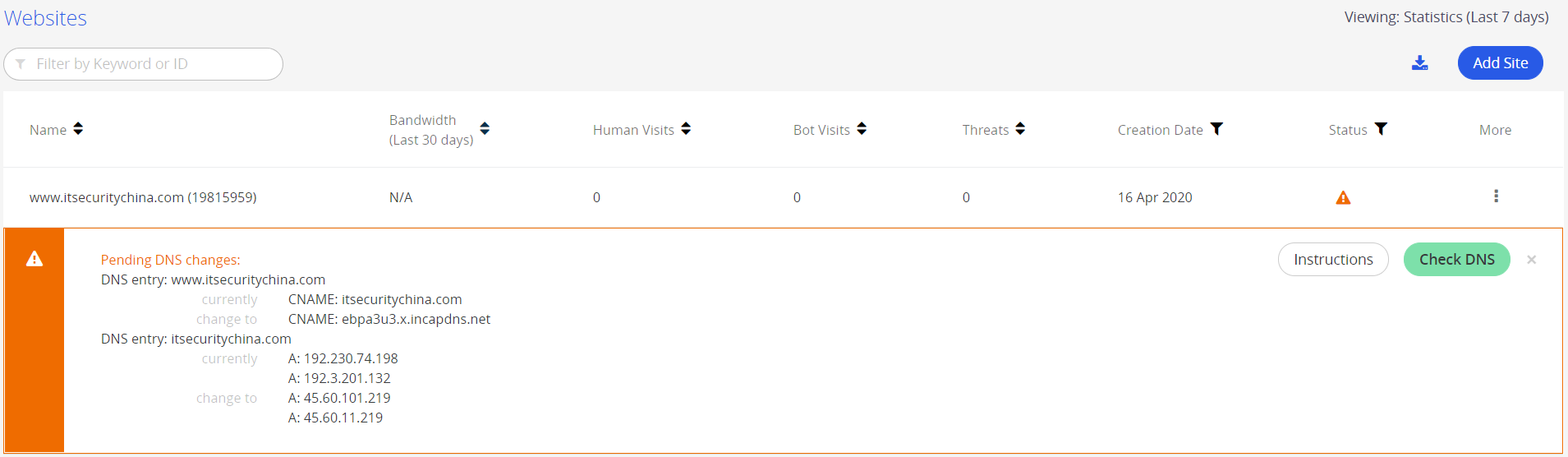
So, jumping over to our zone editor in cPanel let's update a few records. Firstly, the A record for itsecuritychina.com.
Before:
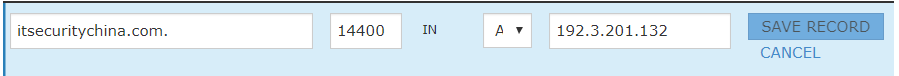
After:
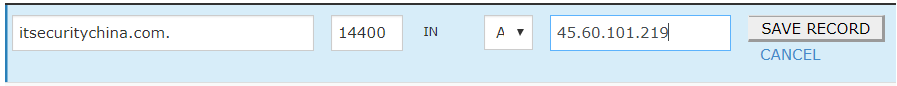
Then we add another A record for a little bit of extra redundancy. This gives us a secondary path to our site if the primary Imperva service fails.
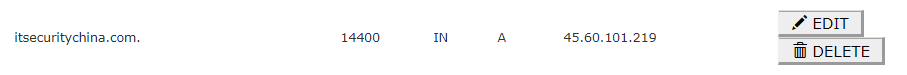
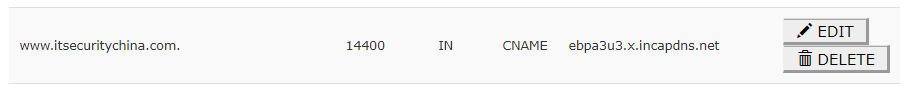
And finally, we are going to update the CName record.
I have an extra A record for 192.230.74.198 which I'm going to delete.
So, we've made all our DNS zone updates. Hitting http://itsecuritychina.com in a web browser now we get ... drumroll please…
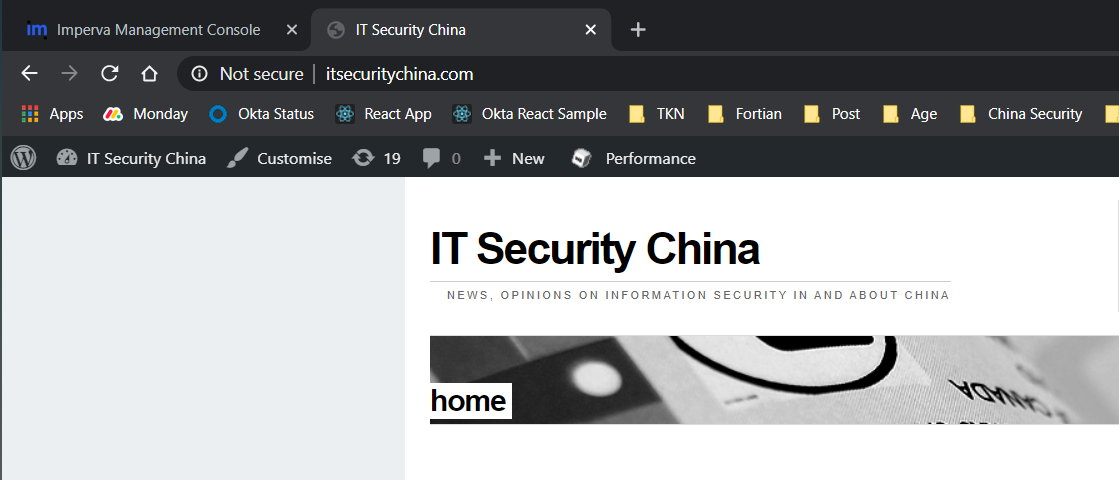
Woo hoo! A working insecure website!
And trying the HTTPS secure version… A working, TLS secured, website!
The last step, back in the Imperva console, click the check DNS button. If the DNS propagation Gods favour you, this will have resolved by now. For me it hadn't so I'm back in the waiting game.
And we're done!
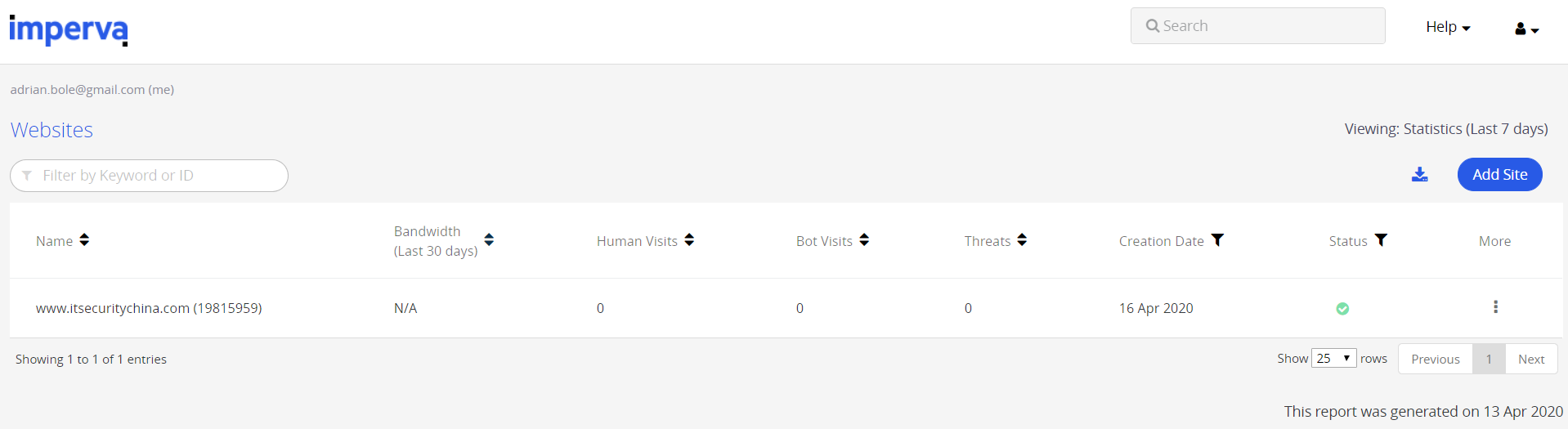
Here's an example of Imperva in action. Unfortunately, it's blocking my legitimate manage ManageWP traffic (a service I use to update and backup my WordPress sites), but it gives us a good example to start see what the WAF can do.
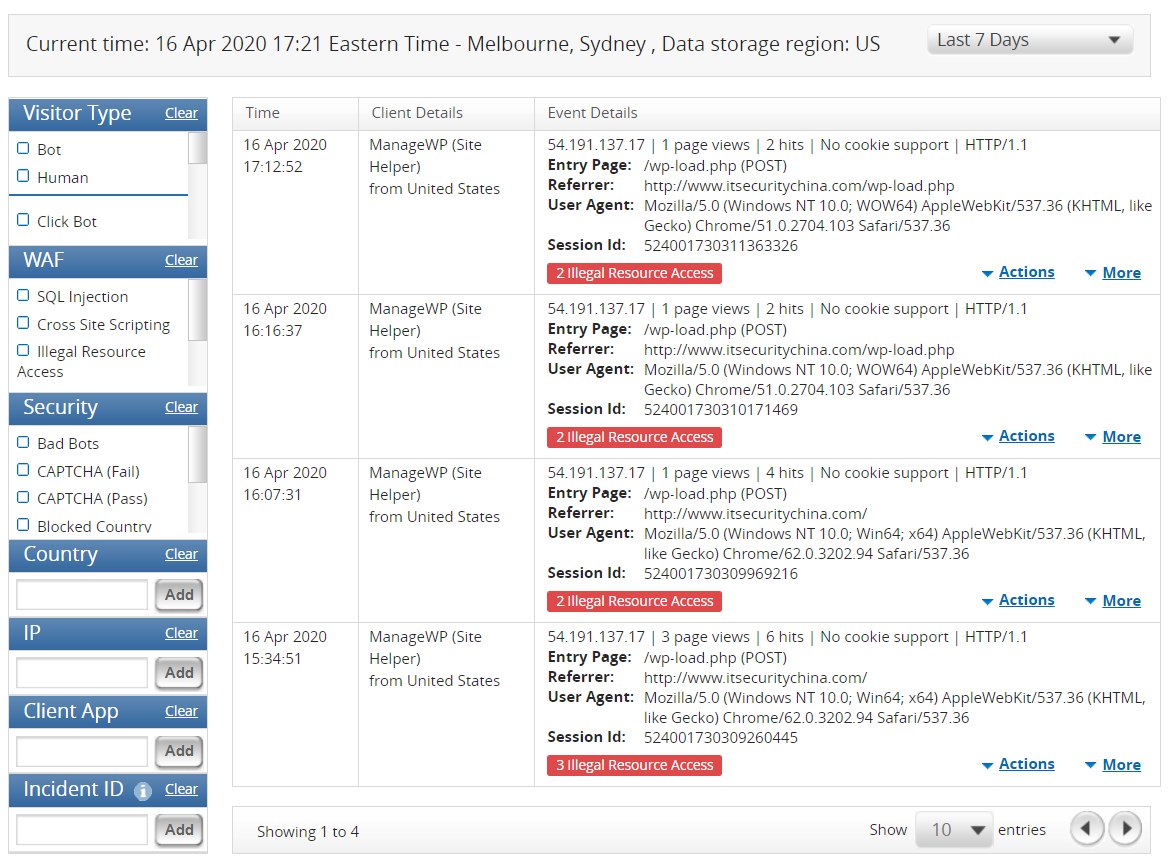
We can drill in for a little more detail on the POST payload, URIs called etc. as well.
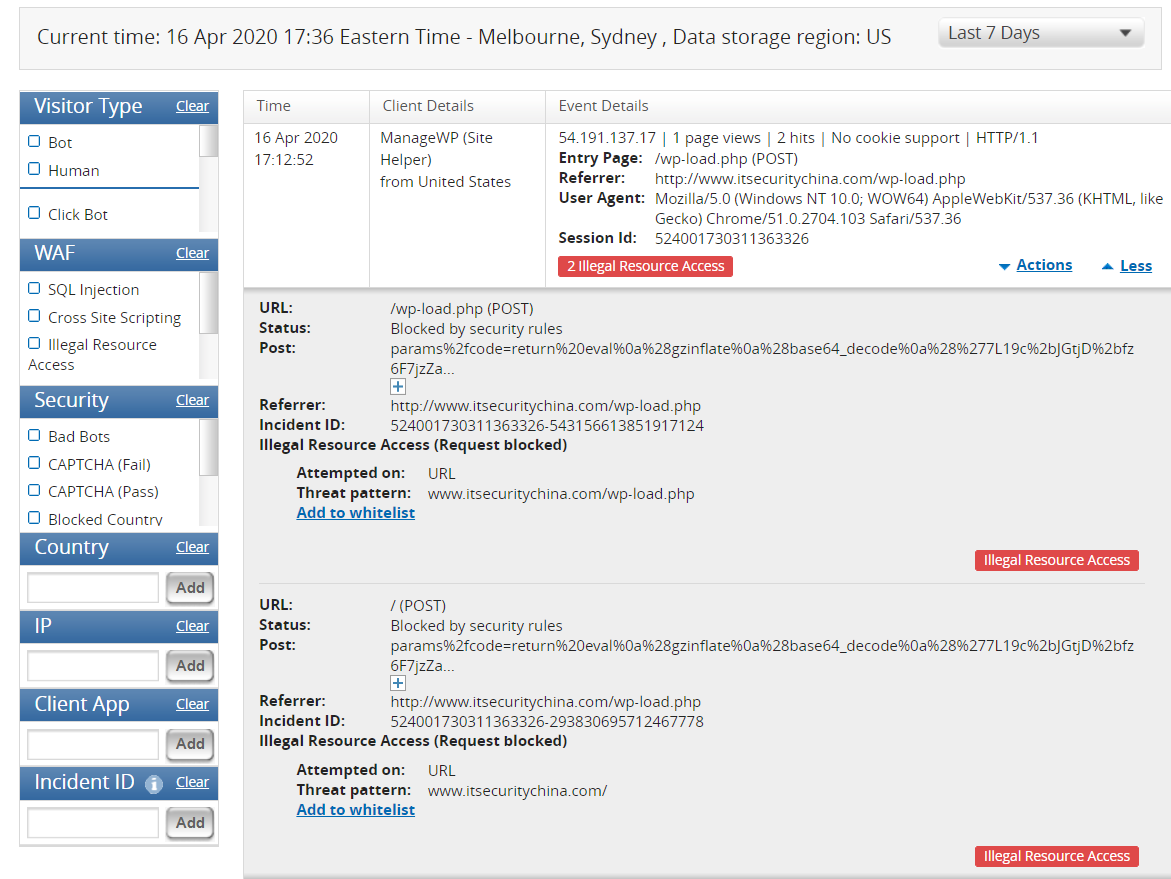
And drill in a little more. If I didn't know this site, my suspicion would be off the charts right now.
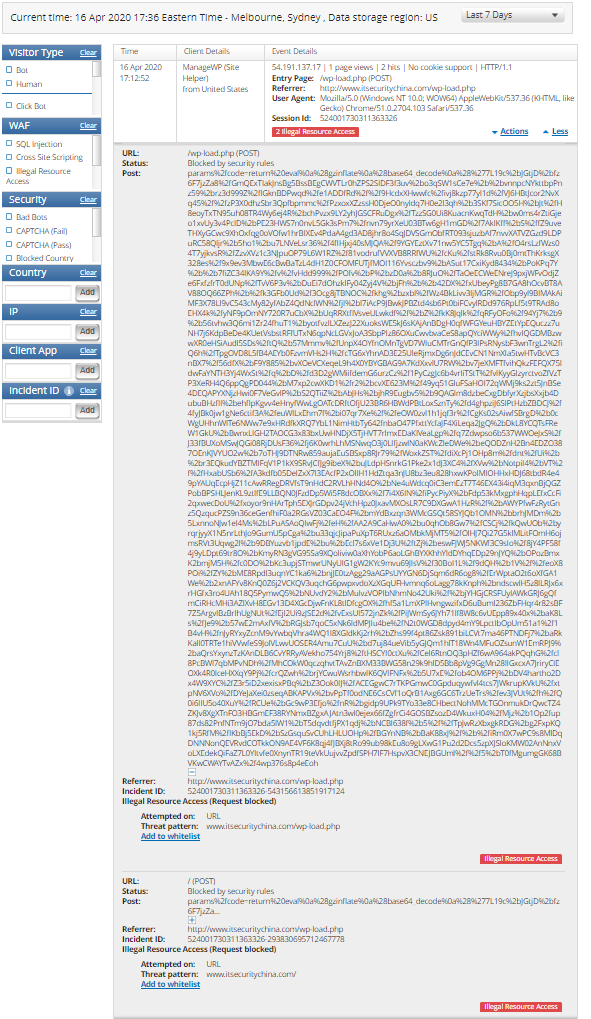
Tip! don't forget if you use any website monitoring or management services whitelist their IP addresses in your WAF. This is unfortunately exceptionally tedious in Imperva as you need to whitelist them one by one.
So that’s a wrap! I’m not exactly an expert in WAFs (and even I could set this up!) but feel free to email me at adrian@fortian.com.au if you have any questions or follow me on twitter @adrianbole. In the next blog we’ll secure access to the Imperva console with an MFA policy using Okta – stay tuned.
Request a consultation with one of our security specialists today or sign up to receive our monthly newsletter via email.
Get in touch Sign up!