Cooper Eldridge, Winter Intern, | August 3, 2023
Over the 2023 winter break, I had the opportunity to partake in a 4-week internship program with Fortian. As someone keen on developing a career in cybersecurity, this was an opportunity I was looking forward to for weeks, and one that I’m excited to share as I write out my experiences now.
I spent my time at Fortian working within their Managed Security Services team, primarily working within their Security Operations Centre (SOC). However, as the four weeks came and went, I realised that I wasn’t exactly working within a traditional SOC. Rather, I seemed to find myself working within a small, but highly specific cyber-zoo, dealing primarily with RATs (Remote Access Tools) and Velociraptors. These two “cyber-creatures” were the focus of my work, with the former becoming the centrepiece of my first significant project.
The project in question was a threat hunt, where I was investigating a client’s environment for evidence to prove or disprove the following hypothesis:
A client device has been compromised by a threat actor, who has installed a legitimate Remote Access Tool (RAT) as a persistence mechanism to stage further attacks on the network.
This project wasn’t just something drummed up to keep me busy, this was a useful investigation for both the business and the client, which I appreciated. It allowed me to feel a sense of purpose and importance with the work I was doing, which was important in keeping my motivation high even when I was encountering challenges. Most of the work I was doing was primarily within Microsoft Sentinel, something I had some experience with due to my past projects I’ve done. However, as I spent my first couple of days working on the report, I encountered my first main problem:
Understanding the sheer volume of tables and trying to figure out what data is located where.
Microsoft Sentinel is set up to ingest a lot of data from the client. Initially I was hung up on the fact I didn’t really know where anything was in the data we had available to us. It was during opportunities to shadow other team members that I realized in cybersecurity, dealing with the unknown—both in terms of 'what' and 'where'—is the norm. Instead, having a strong problem-solving methodology and an inquisitive mindset were the two most important tools you could have. I often ran into situations where RATs were doing things I didn’t understand, but by taking the time to explore and play with the data, I was able to paint a better picture and have better confidence in reporting what I was finding.
The threat hunt provided a great opportunity for me to develop my skills within Microsoft Sentinel and the Kusto Query Language (KQL) it uses. Many of the RATs I found executing on client devices were doing a variety of abnormal and interesting things, so taking the time to investigate each one was perfect to learn the ins and outs of Sentinel and using KQL. I was able to gather many intriguing findings, all reported in a threat hunt document that ultimately was sent out to the client. It gave me an opportunity not only to develop my skills with Microsoft Sentinel and KQL, but also develop my report writing skills. The shift from writing papers for university to a professional report was significant, so getting feedback on my attempts there was immensely valuable in learning to be a proficient communicator in a corporate setting.
Having said that, not all the data that I would’ve liked to access for the threat hunt was available through Sentinel. I wanted to try investigating log files that contained the IP addresses that RATs were connecting to, but Sentinel did not have this information available. This provided the perfect transition into working with Velociraptor, a digital-forensics tool that can increase the visibility we have into client endpoints. It can create remote collectors, that when run on a device, can harvest forensic artefacts of interest. Velociraptor was able to collect and analyse the log files RATs created, filling a gap in Sentinel’s data availability.
It wasn’t completely efficient though, as the collectors need to be put onto a machine, manually run, then the zip file containing the results needs to be sent back to the security team. Asking the client to do all these manual steps is far from seamless, so there was room for improvement. From there, it seemed like a good idea to have a power shell script to automate the running of the velociraptor collector. It downloads it from an Azure container, runs the executable, uploads the data to a write once, read many (WORM) container in Azure, then delete itself from the system. A lot more streamlined, but still, there’s room for improvement.
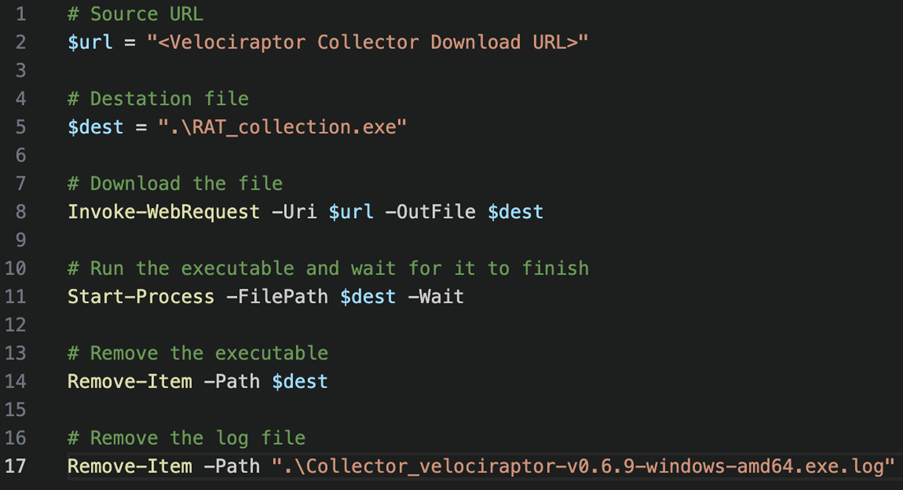
The next layer involves Microsoft Defender’s Live Response functionality. A Live Response session can be started on a device through Defender, which allows remote execution of PowerShell scripts once it’s uploaded to the Live Response Library. This completely removes any manual input from the client, safeguarding the collection process from having a client accidentally edit or interrupt it. Starting out a Live Response session through Defender is not the most streamlined process however, taking significant time to navigate through menus and connect, which is not ideal.
This brings me to the final layer of automation, which involves the use of Azure Logic Apps to automate the whole Live Response process with a single press of a button. The current iteration runs on an entity, so when a device is involved in an incident, the playbook can be launched against it. The playbook handles running the Live Response, allowing the security analyst investigating the incident to swiftly investigate and respond to potential threats.
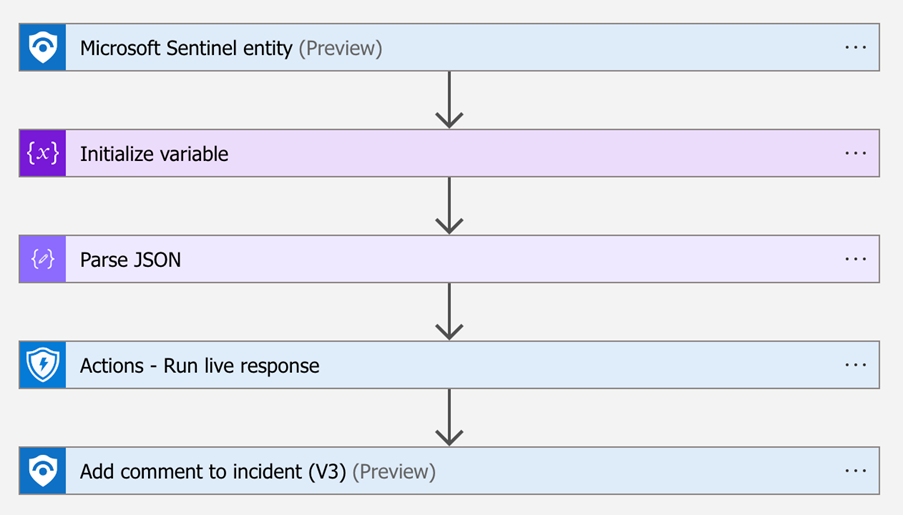
Troubleshooting this project brought me to the end of my time with Fortian, and while I couldn’t finish it, the learning I gained from getting hands on with the tools was invaluable. Fortian’s collaborative culture allowed me to freely work together with the entire team, with them showing genuine interest in the work I was doing. It was a pleasure to work with the team over the winter break, and I would highly encourage those thinking of interning at Fortian to apply. It’s a workplace full of great people, dynamic work, and has been one of the highlights of the year for me, for which I am truly grateful for such a rewarding experience.
Request a consultation with one of our security specialists today or sign up to receive our monthly newsletter via email.
Get in touch Sign up!