Riva Antonio and Prashanth B.P. | Fortian Security Consultants | 17 January 2025
Business email compromise scams are a common style of attack that Fortian's Security Operations team actively monitors and helps our customers defend against.
However, a recent Western Australian District Court decision around who should bear the liability for losses over a business email compromise scam highlights the need for organisations paying invoices to take active steps to ensure that payment details are correct.
In this particular case, the Court held that even though the payee’s email system was hacked and account details changed via email, the organisation paying the invoice was obliged to take active steps to verify that the account changes were legitimate. Because the payer didn’t take sufficient steps to verify the account changes, it was liable for the loss.
This blog post aims to outline what happened, the nature of the dispute, the Court decision and implications for Australian organisation, including ways that organisations can protect themselves.
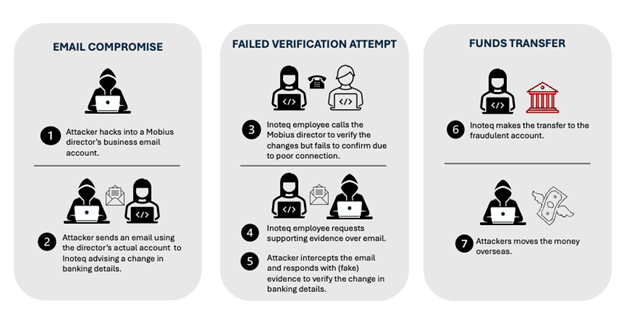
In January 2022, Mobius Group, an electrical instrumentation and control systems contractor was hired by Inoteq, to carry out electrical work on a Rio Tinto project. This work was completed in accordance with the set agreement. In March and April 2022, Mobius sent two invoices to Inoteq, totalling $235,400.29.
Before the invoices were paid, a hacker gained access to an email account that belonged to a director of Mobius. Using this compromised account, the hacker sent a fraudulent email to Inoteq, falsely claiming that Mobius’ payment details had changed. The email included a fake invoice with altered bank account information.
When Inoteq attempted a follow-up call with Mobius to confirm the changes, the call was unsuccessful due to a poor connection. Inoteq then requested, via email, proof of the account change, such as a formal letter or documentation on Mobius’ letterhead. Shortly after, Inoteq received a reply from the compromised email account which included an attachment that appeared to be on letterhead confirming the new bank details. However, both the email and attachment were fraudulent, created and sent by the hacker.
Relying on the fraudulent email, Inoteq approved the updated bank details and transferred the funds to the nominated account. This bank account was set up by the fraudster under the name of an unsuspecting individual. It was then transferred overseas.
It was only later, when Mobius followed up Inoteq on the payment, the fraud was discovered. While the bank managed to recover $43,451.13, most of the money was lost.
Mobius, having not received the payment, initiated legal action to recover the outstanding balance, $191,859. Inoteq disagreed, arguing that an indemnity clause covers fraud-related losses, and that Mobius had a duty of care to secure its email system. Inoteq also argued that Mobius was a concurrent wrongdoer as it failed to secure its email system and as such, its liability should be reduced.
Judge Gary Massey ruled that Inoteq was still liable to pay Mobius for the unpaid invoices, plus six percent interest per annum.
Massey found that the indemnity clause did not require Mobius to cover Inoteq’s loss from a fraudulent payment, as the loss was caused by an external hacker and not related to the services outlined in the contract.
Moreover, Massey determined that “the duty of care claimed to exist by [Inoteq] does not apply to the circumstances of this case”. Massey found that “whilst the actions of the fraudster are reprehensible, ultimately [Inoteq] was in the best position to protect itself against the fraud” and that the failure to take adequate precautions, such as making a follow-up call after the initial confirmation attempt failed, rested with Inoteq. In forming his view, Massey found that there was an absence of evidence as to how costly the protection of Mobius’ email system would be along with the practicability of its implementation, which in turn weighed against imposing the duty of care claimed by Inoteq.
This decision, whilst seemingly unfair due to the fact that Mobius’ email system was hacked in the first place, reinforces the need for Australian organisations to be incredibly vigilant when it comes to the payment of invoices. To prevent such attacks, organisations should consider the following security controls:
Sources:
Request a consultation with one of our security specialists today or sign up to receive our monthly newsletter via email.
Get in touch Sign up!