Jake Astles, Security Consultant (jacob@fortian.com.au) | Oct 27, 2019
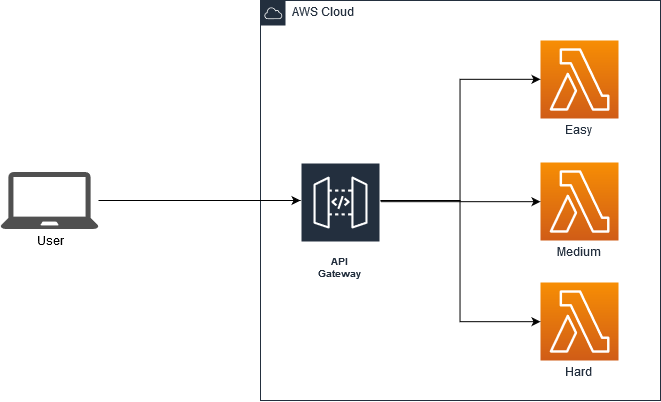
In this post we are going to run through the set up and configuration used to create this year’s Fortian Technical Security Challenge at AISA CyberCon. You can read part 1 here.
The aim of this post is to provide a quick look at how AWS serverless infrastructure can be used to quickly host a website with backend logic and a custom domain and associated certificates.
As mentioned in the previous blog post, the Challenge involved a series of Capture The Flag (CTF) puzzles. Completing each puzzle provided a flag, as well as a hint towards how to obtain the next flag.
The Challenge was hosted on Amazon Web Services (AWS) using the API Gateway and Lambda services. Additional services used include Route53 for the custom DNS and domain name and Certificate Manager for the TLS certificate.
Lambda functions can be created from the Lambda Service page. This can be found under the Compute heading or by using the search box. When creating the Lambda first, there is the option to use a Blueprint. The “microservice-http-endpoint” blueprint will automatically create a Lambda function as well as the API Gateway and perform the necessary linking and permissions.
When authoring the function from scratch, give the Lambda a useful descriptive name such as “Fortian_CyberCon_Challenge_2019_Easy” and select a development language. This challenge was written using Python 3.7. To ensure that the Lambda has permissions to connect and share with an API Gateway, use the built-in role of “service-role/api_role”. The challenge consisted of two more Lambdas, one for the medium and one for the hard flags.
Heading over to the API Gateway, if the API was created as part of the blueprint, there is nothing left to do other than deploy it. Deploying the API will automatically create an amazon.com based URL. When creating a new API Gateway from scratch, the HTTP methods must also be created:
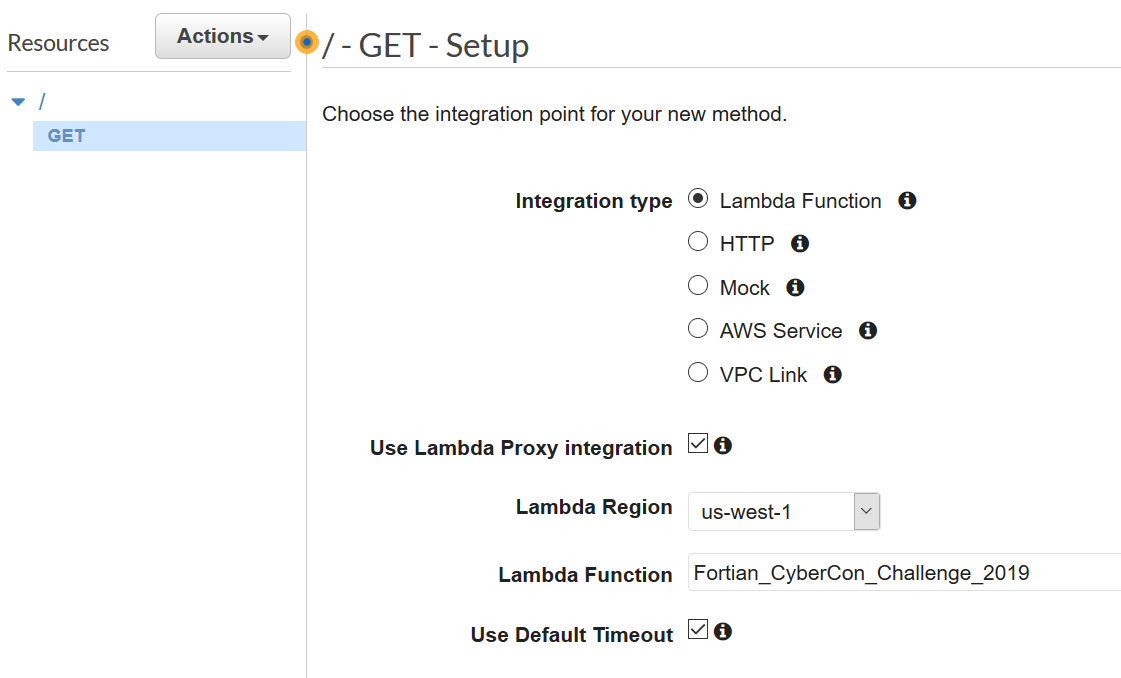
The Integration type of “Lambda Function” allows the API to connect and call the Lambda function created earlier. Because the Lambda returns HTML that needs to be rendered. The “Use Lambda Proxy integration” checkbox needs to be selected. The “Lambda Function” is an autocomplete field for existing Lambda functions.
The challenge made use of one API resource and associated methods per flag or Lambda function.
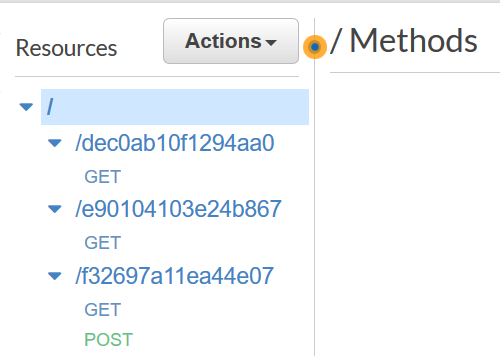
The easy and medium challenge Lambda functions contain some basic python to simply return a static HTML page and therefore only need GET requests:
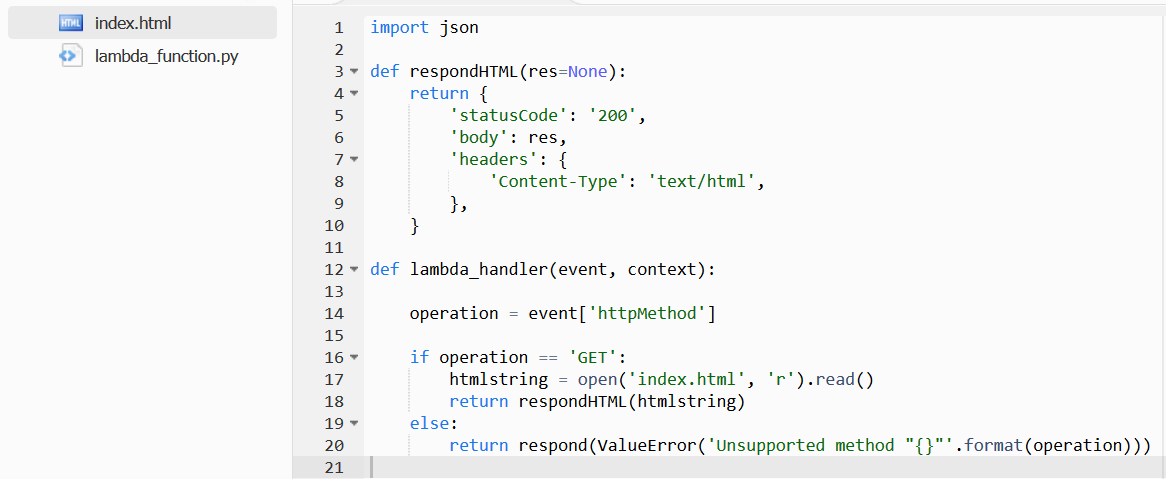
This code checks to make sure that only a GET request will return a valid response. The GET request simply reads the local index.html file and returns it with the necessary response headers for the browser to render the page.
The hard challenge included a login form. In order to obtain the final flag, users had to enter a password uncovered along with one of the other flags. Because of this, the function and API must also include handers for POST requests.
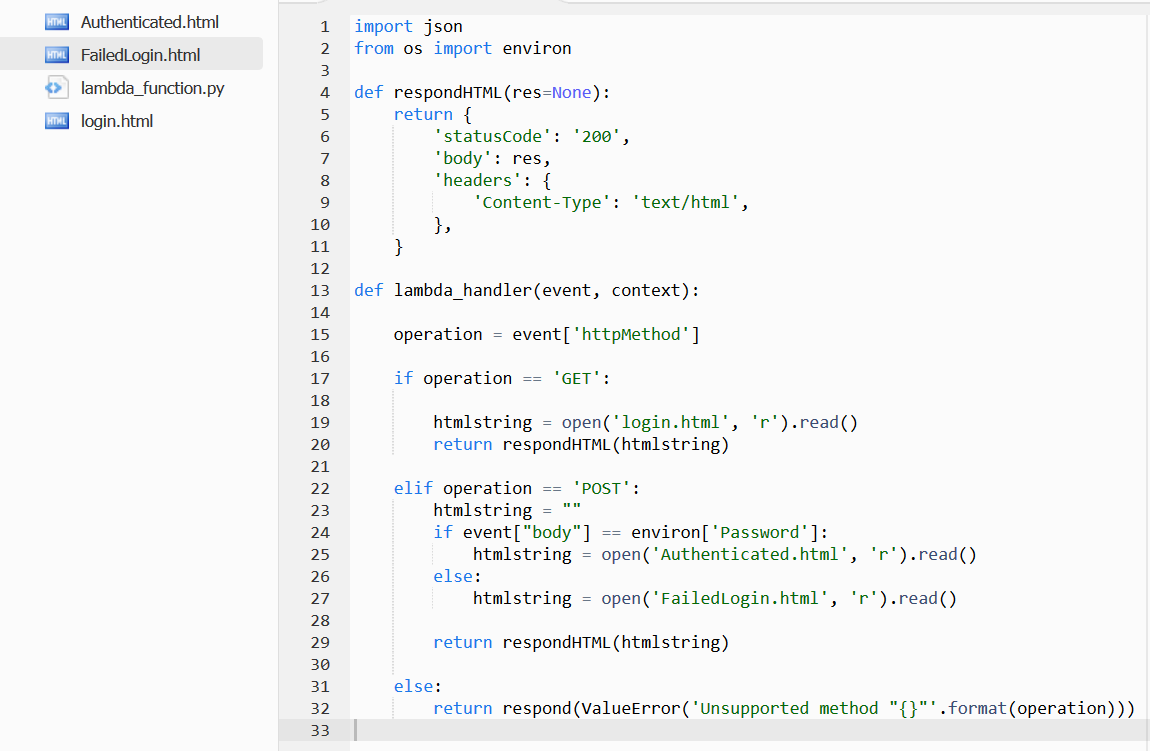
The ‘event’ object contains details of the request and can only be used if Lambda proxy integration was checked for the API method. This object is used to handle the GET and POST requests appropriately. GET requests return the login page. The login.html page contains a form that Base64 encodes the user’s input and sends a POST request back to the same API endpoint and Lambda. When the Lambda receives a POST request it compares the password entered by the user to the correct one that has been stored as an Environment variable. A correctly entered password will return the authenticated.html page containing the final flag.
By default the API Gateway will be given an amazon.com subdomain such as https://di73l54aig.execute-api.us-west-1.amazonaws.com/default. A custom domain and associated certificates add a more authentic feel to the challenge.
Domains can be purchased and registered within AWS or through any domain registrar. Once a domain has been purchased. Use AWS Certificate Manager to create a certificate with the required subdomain. This process will prompt for different types of validation to ensure that you are allowed to generate a certificate for the requested domain. If the DNS was purchased through AWS, DNS validation allows quick and easy linking of the certificate to the domain including a button to automatically create the associated Route53 record for the subdomain.
While the certificate is created and validates, it needs to be linked to the API Gateway. From the API Gatewaymanagement page, the Custom Domain Names option can be used to set up custom subdomains and base paths for the API. When creating the custom domain name, the certificate can be selected from the drop-down list. This certificate will be used for the API subdomain and any base path mappings.
Once complete users will be able to browse to the site using the custom domain, in this case https://challenge.fsbox.org/
Request a consultation with one of our security specialists today or sign up to receive our monthly newsletter via email.
Get in touch Sign up!