Koushik Anand Pirabu, Winter Intern | 1 October 2024
During the 2024 winter break, I had the opportunity to complete a 3-week internship that offered hands-on experience in a field I am deeply passionate about. As an aspiring cybersecurity professional, I was excited to dive into real-world projects and enhance my technical skills in a professional environment. Reflecting on my time now, I’m eager to share the experiences and outcomes I gained at Fortian.
Similar to past interns, I also worked alongside Fortian's Managed Security Services (MSS) team in their Security Operations Centre (SOC) space. My work, in particular the major project, greatly reflected the diverse skillsets of the MSS team, in particular their ability to perform incident response (IR) on a multitude of threats across unique clients and environments. Consequently, IR became the centrepiece of my major project.
The project in question had two main areas of focus:
A live response session in XDR allows analysts to remotely access a compromised device to extract information and files for further analysis.
Given this can be automated via PowerShell scripts, and my limited prior knowledge of PowerShell, this was a great opportunity to learn a new language in a practical manner.
The first script involved extracting files placed in quarantine by Defender for analysis. The challenge came from Defender encrypting all files in the quarantine folder, making file analysis without decrypting them impossible! Initially, I struggled with figuring out the type of encryption used by Defender. However, from shadowing other analysts, I realised that alongside technical skills, being exceptionally curious by conducting thorough research is a vital skill to possess when dealing with the 'unknown', which is often the case in cybersecurity and precisely why this field fascinates me so much.
Therefore, by utilising the knowledge of my team members and various whitepapers and academic research, I was able to paint a better picture of the precise workings of Defender's quarantining mechanisms and understand the structure and flow of the script.
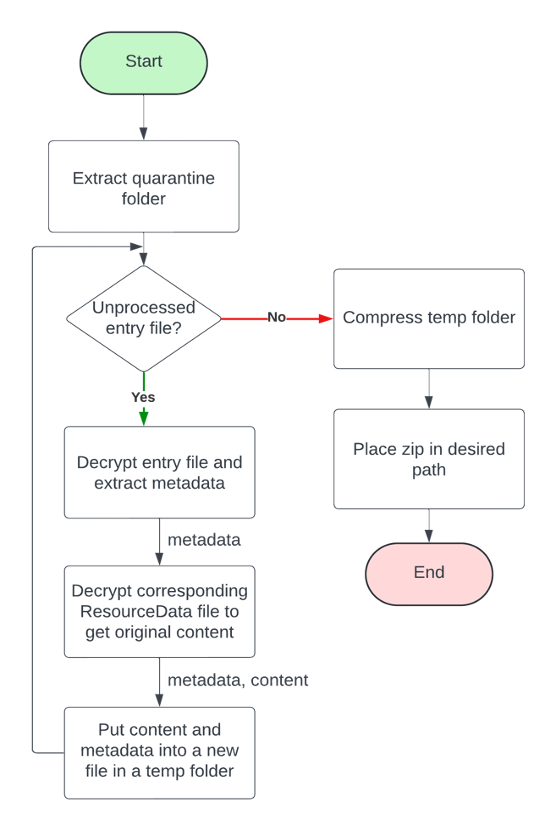
A particularly noteworthy part of the script-building process was in the MSS team's sandbox environment, I was able to download *real malware samples* and trigger Defender's quarantine process to not only understand the quarantine process but also test the script with malicious data to determine its efficiency and make further refinements.
The second script involved dumping the memory of an application into a file. This is useful in cases where fileless malware (malware that primarily resides in memory) is suspected and an analyst would like to examine the memory of a process. The major challenges for this primarily involved finding and understanding the right PowerShell functions to simplify this process. Another point of consideration was the file size of the dump file, as memory-intense processes like web browsers would cause PowerShell to crash during the memory writing process. Similar to the previous script, performing **thorough research** and **experimenting with various iterations** of the script was invaluable in finding the solution.

This part of the project involved writing detection rules within Microsoft Sentinel using the Kusto Query Language (KQL). The specific scenario to detect for was:
The use of Rclone to exfiltrate data from a compromised device.
Given that Rclone is typically used to exfiltrate data from the network, it was logical to inspect the network activity logs in Sentinel to glean information. However, Sentinel is set up to ingest immense amounts of data from the client, and finding specific information from the various log tables can be intimidating. Similar to the scripts, performing research and experimenting with the various tables using sample queries greatly helped to pinpoint the relevant tables and datasets while providing a greater understanding of the power of log analytics in incident response.
In essence, the detection query, done in KQL, looks for networking activity initiated by rclone, and flags ones deemed to be malicious based on the flags passed into rclone by the user that suggests with high confidence that it's being used for data exfiltration. The additional detection parameters reduce the possibility of false positives and maintain a wide-enough scope to detect usage with malicious intent.
Similar to the first script, I was able to conduct testing of the query by initiating file transfers using rclone to temporary Mega and Jottacloud servers and observing the query's response. This process interestingly allowed me to imitate a threat actor's mindset by trying to find ways to successfully exfiltrate data without raising suspicion, which allowed for further refinements of the detection rule and led to a fulfilling experience of simulating a red and blue teaming exercise.
The completion of the detection rule brought me to the end of my internship at Fortian, and I’m incredibly grateful for the hands-on experience I gained. The project wasn’t just an academic exercise conjured up to keep me busy — it directly contributed to the company’s ability to protect its clients from evolving cyber threats.
Fortian's inclusive nature gave me the perfect environment to work alongside passionate security professionals who showed genuine interest in my work and were always willing to provide guidance and advice. I could not have asked for a better internship experience, and I highly encourage anyone interested in cybersecurity to consider interning at Fortian. It is a workplace with amazing people, an inclusive culture and a genuine passion for security and I am thankful for such a rewarding experience.
Request a consultation with one of our security specialists today or sign up to receive our monthly newsletter via email.
Get in touch Sign up!